By Product Marketing
As the cyberthreat landscape grows more complex and cybercriminals take advantage of emerging technologies and new vulnerabilities, enterprises must tread carefully as they confront the challenge of protecting their platforms from evolving bot threats while maintaining smooth access for legitimate users.
Real customers drive real revenue
These advanced bots can cleverly imitate human behavior to slip past conventional defenses, posing serious challenges for enterprises. They disrupt customer experiences, place a strain on resources, and ultimately have a detrimental effect on revenue.
As such, enterprises must ensure that they have the ability to accurately distinguish legitimate users from bots. Whether it’s a customer signing up for a service, making a purchase, or engaging with a platform, ensuring these interactions are frictionless is key to maintaining trust and driving growth.
On the other hand, bots generate fraudulent traffic that wastes bandwidth, drains server resources, and skews analytics, diverting attention and investment from real opportunities.
Furthermore, bots often flood platforms with non-customer requests, overloading systems and driving up infrastructure costs. If left unchecked, this activity not only erodes performance but also inflates operational expenses.
Accurate human user detection allows enterprises to allocate resources efficiently, ensuring they are focused on supporting real customers rather than processing illegitimate traffic.
As cybercriminals continue to deploy more sophisticated bot strategies, enterprises need more than basic security measures like CAPTCHAs or IP blocking. What is needed is an intelligent, adaptive approach that adds an extra layer of defense to traditional defenses to reliably identify human users.
The Challenge of Distinguishing Human Users
Detecting human users is far from straightforward. While many organizations rely on tools such as Web Application Firewalls (WAFs) and DDoS protection systems, these technologies are not designed to differentiate humans from bots.
- WAFs: Primarily protect against OWASP Top 10 threats such as SQL injection and cross-site scripting. They focus on known attack vectors but lack the ability to analyze user behavior in real time.
- DDoS Protection Systems: Designed to identify and mitigate volumetric attacks. These systems may detect high traffic loads from malicious bots but are not equipped to assess the nuances of individual user interactions.
These limitations leave organizations vulnerable to advanced bots that can mimic human behavior, bypassing traditional defenses and creating challenges in safeguarding applications, APIs, and resources.
Common Bot Detection Techniques
There are several mainstream techniques that are used to detect malicious bot actiivty.
- Human User Accuracy: How effectively the technique distinguishes between human users and bots.
- User Experience (UX): How seamless and frictionless the technique is for legitimate users.
Below, we explore common detection techniques, their pros and cons, and compare them to Visitor Behavior Tracking—an advanced approach designed to adapt to modern bot challenges.
Detection Solutions
A variety of detection techniques are commonly used to identify human users, each with its strengths and limitations. Basic CAPTCHAs, for instance, require users to solve simple challenges, such as identifying images or entering text.
While effective against basic bots, advanced bots equipped with machine learning or human solvers can easily bypass CAPTCHAs, making this method increasingly unreliable. Furthermore, CAPTCHAs often frustrate legitimate users, particularly those on mobile devices or with accessibility needs, leading to poor user experience.
Static behavioral analysis is another method that relies on fixed patterns, such as mouse movement speed or click timing, to detect bots. Although minimally disruptive for users, this approach struggles against bots capable of mimicking human-like behaviors, leading to inaccuracies over time.
Similarly, User-Agent analysis examines HTTP headers to identify bots, but this technique is easily spoofed by bots, rendering it insufficient as a standalone solution. Cookie-based tracking is slightly more robust, as it monitors user behavior across sessions. However, it is vulnerable to cookie deletion, private browsing, and manipulation by bots, limiting its reliability in modern environments.
Reputation-based systems offer another approach, leveraging historical data to classify users or IP addresses as legitimate or malicious. While these systems can be effective for known threats, they often fall short when faced with new or unknown bot profiles.
Machine learning is also frequently employed, using predictive algorithms to distinguish bots from humans. However, the accuracy of this method heavily depends on the quality of the training data. Poorly trained models can misclassify users, creating both false positives and false negatives.
Blocking Solutions
Blocking solutions are often used as a first line of defense against bots, but their simplicity can sometimes lead to unintended consequences. For instance, simple IP blocking aims to prevent access from known malicious IP addresses.
However, this approach is easily circumvented by bots using rotating IPs or proxies, and it risks blocking legitimate users who share IP ranges with bad actors. As a result, its effectiveness is limited, especially against sophisticated bot networks.
Geolocation checks are another blocking method, designed to restrict traffic from specific geographic regions. While potentially useful for targeting region-specific threats, this technique has significant drawbacks.
Bots often use VPNs or proxies to mask their true location, rendering geolocation checks ineffective. Moreover, these checks can inadvertently exclude legitimate users from the targeted regions, leading to poor user experience and reduced accessibility.
Rate Limiting Solutions
Rate limiting is a commonly implemented solution to control traffic volumes by restricting the number of requests a single IP or session can make within a specific timeframe. While this technique can reduce the overall activity of bots, it often sacrifices user experience in the process.
Legitimate users generating high levels of traffic—such as those navigating quickly through an application or conducting large transactions—may find themselves inadvertently blocked. This blunt approach lacks the nuance needed to address the sophisticated behavior of modern bots while ensuring seamless access for genuine users.
Comparisons of Detection, Blocking, Behavioral and Rate Limiting Solutions and their Accuracy and UX in Bot Management
| Group | Technique | Human User Detection Accuracy | User Experience |
| Detection Solutions | Basic CAPTCHA | Low | Poor |
| Static Behavioral Analysis | Low to Moderate | Moderate | |
| User-Agent Analysis | Low | Excellent | |
| Cookie-Based Tracking | Moderate | Good | |
| Reputation-Based Systems | Moderate | Good | |
| Over-Reliance on Machine Learning | Varies | Moderate | |
| Blocking Solutions | Simple IP Blocking | Low | Poor |
| Geolocation Checks | Low to Moderate | Poor | |
| Behavioral Solutions | JavaScript Challenges | Moderate | Good |
| Session Management | Low to Moderate | Good | |
| Visitor Behavior Tracking | High | Excellent | |
| Rate Limiting Solutions | Basic Rate Limiting | Moderate | Poor |
Table 1: Comparisons of human user detection technique
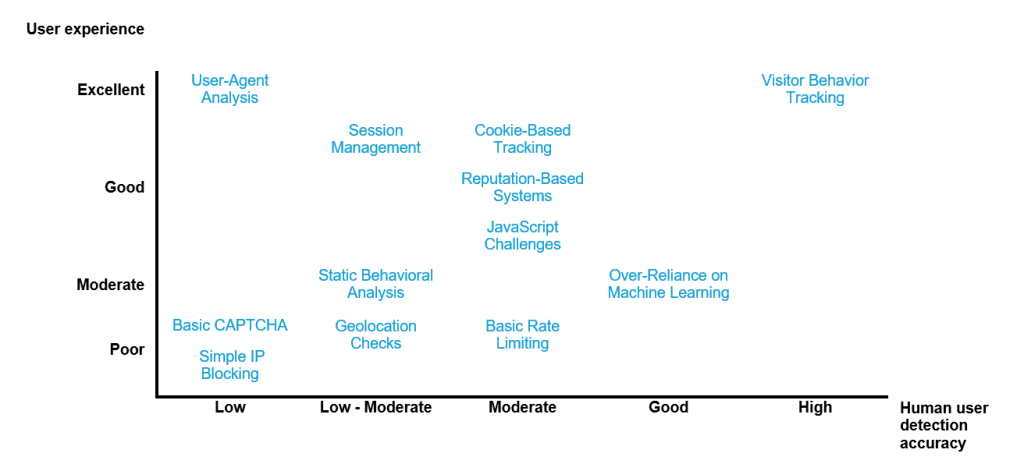
Diagram 1: Comparisons of human user detection technique.
As bots grow more sophisticated, the limitations of traditional techniques like CAPTCHAs, IP blocking, and rate limiting become clear. While useful in specific cases, these methods often disrupt user experience and struggle against advanced bots.
Visitor Behavior Tracking, such as IntelliFend’s VisitorTag, is essential for effective bot management but achieves its full potential when combined with complementary techniques. A comprehensive, multi-layered solution ensures accurate human user detection, manages both good and bad bots, and optimizes security, user experience, and resource efficiency.
Take the Next Step
Human user detection is just one piece of the puzzle. Discover how IntelliFend’s VisitorTag Tracking Technology and AccuBot Detection Engine seamlessly work together to deliver precise human user detection, forming the backbone of an advanced and effective bot management system.
Check out our next blog: How IntelliFend’s AccuBot Engine and VisitorTag Technology Work